
 By Admin
By Admin Protecting Digital Assets Through Software Development Security
Introduction
As technology continues to transform the way we live and conduct business, software applications have become the backbone of the digital world. From mobile apps to web services and enterprise software, these applications drive innovation and connectivity. However, with the ever-increasing reliance on software, the risks associated with cyber threats and attacks have also grown exponentially. Software development security plays a crucial role in protecting digital assets, user data, and overall system integrity. In this blog, we will explore how software development security works and the significant ways it helps safeguard the digital frontier.
Understanding Software Development Security
Software development security is a multifaceted approach that integrates security measures and best practices into the entire software development lifecycle. It focuses on identifying potential vulnerabilities, addressing security risks, and mitigating the impact of security breaches. This proactive approach helps in building applications that are robust, resilient, and resistant to attacks.
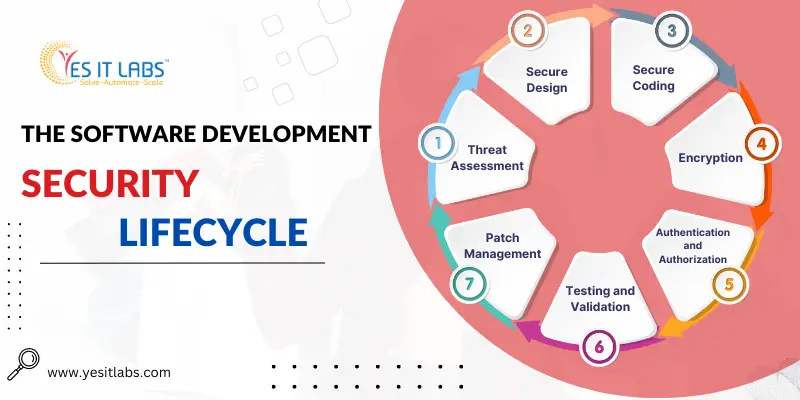
The Software Development Security Lifecycle
- Threat Assessment: The process begins with a comprehensive threat assessment where developers and security professionals identify potential risks and threats that the application might face. This involves understanding the application’s architecture, design, and functionality to identify potential entry points for attackers.
- Secure Design: During the design phase, security requirements are integrated into the application’s blueprint. Security experts collaborate with developers to ensure that the design can withstand potential attacks and that sensitive data is protected at all stages.
- Secure Coding: Writing secure code is at the heart of software development . Developers must adhere to secure coding guidelines and best practices, avoiding common pitfalls such as injection attacks, insecure authentication, and poor data validation.
- Authentication and Authorization: Proper authentication mechanisms are put in place to verify user identities and prevent unauthorized access. Multi-factor authentication (MFA) is often implemented to add an extra layer of security. Additionally, robust authorization controls ensure that users can access only the functionalities and data they are allowed to see.
- Encryption: Data encryption is a critical aspect of software development. Sensitive data, both at rest and in transit, is encrypted to prevent unauthorized access. Encryption algorithms and protocols like SSL/TLS ensure data confidentiality and integrity.
- Testing and Validation: Throughout the development process, rigorous security testing and validation are performed. This includes static code analysis, dynamic application security testing (DAST), penetration testing, and vulnerability assessments. These tests help identify and rectify security flaws before the application is deployed.
- Patch Management: Once the application is released, the work on security doesn’t end. Regular updates and patches are issued to address newly discovered vulnerabilities and keep the application secure against emerging threats.
How Software Development Security Helps
- Protects Sensitive Data: In an era where data breaches are prevalent, software development ensures that sensitive user data, such as personal information and financial details, remains protected from unauthorized access.
- Maintains User Trust: Users are increasingly conscious of their online security and privacy. By demonstrating a commitment to software development, developers instill confidence in their users, fostering long-term trust and loyalty.
- Prevents Financial Losses: Cyberattacks and data breaches can have severe financial implications for businesses. Investing in software development can help avoid costly legal actions, financial penalties, and reputational damage.
- Ensures Regulatory Compliance: Many industries are subject to strict regulatory standards concerning data protection. By adhering to software development security best practices, organizations can achieve and maintain compliance with relevant regulations.
- Reduces Downtime: Cyberattacks can cause significant disruptions to business operations. Software development measures help prevent successful attacks, reducing downtime and ensuring continuous service availability.
- Minimizes Damage from Security Breaches: No system is entirely immune to attacks, but robust security measures can help minimize the damage caused by successful breaches. Quick detection and response are vital to limit the impact on users and the organization.
Conclusion
In the digital age, software development security is not an option; it is a necessity. The rapid evolution of cyber threats demands a proactive and holistic approach to safeguarding software applications. By integrating security into every stage of the software development lifecycle, developers can build applications that withstand the ever-growing array of cyber threats. Software development security helps protect sensitive data, maintain user trust, and mitigate the financial and reputational risks associated with security breaches. Ultimately, the proactive investment in software development security enables businesses to navigate the digital frontier with confidence and resilience.
Latest Resources
Transforming Your Shopify Store with Node.js App Development
April 30, 2024
Xamarin Trailblazers: Pioneering the Future of Mobile Apps
April 29, 2024
























 Services
Services


